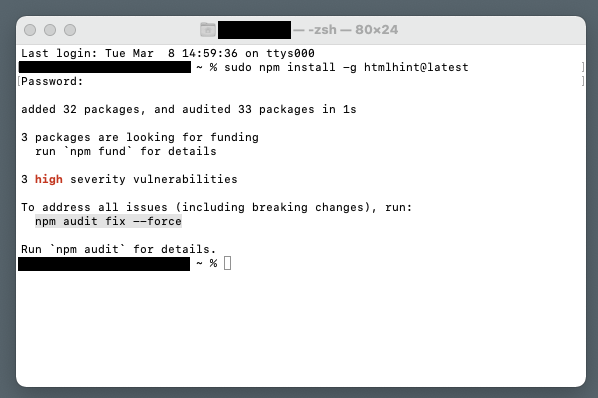
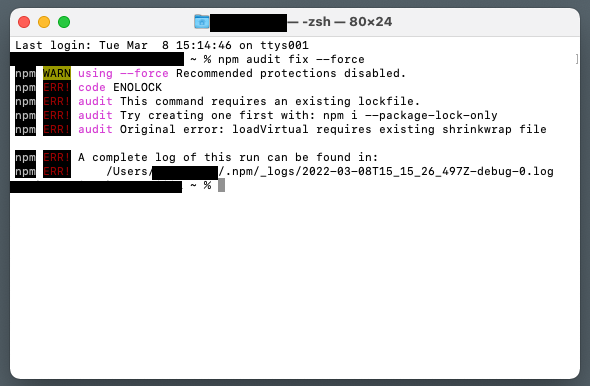
The problem is ultimately related to Node.js and it’s package manager NPM. The way NPM works is that it informs end users about any vulnerabilities in the installed package (whether they are just potential or actual). The fact that you get a warning about a vulnerability doesn’t necessary mean you’re exposed to a direct risk, but the package(s) being listed do contain intrinsic vulnerabilities which may be exploited by malicious third parties.
The point is that if you decide to install Node.js you sort of have to live with that because you’ll inevitably end up getting these notices. Often a package which wasn’t flagged as containing a vulnerability will end up being flagged after an update (of the package or NPM) because a new vulnerability was discovered in the meantime, so the package(s) no longer passes the security test.
Node packages rely on other packages, so it’s common to bump into such notices, especially if the flagged package is no longer being updated by its creator (which is often the case). Also, Node.js has a fairly fast development cycle, so unmaintained packages can quickly end up being flagged, e.g. if they use features which have become deprecated.
These problems are not exclusive to Node.js/NPM, for the same principles apply to any language which uses a package manager. At least NPM informs you about them. But possibly with NPM the situation is somewhat accentuated because there is a tendency to overuse third party packages even for simple tasks — a well known example of this was NPM’s “left-pad”, a package consisting of 11 lines of code to handle text padding; when in 2016 the package was deleted the entire Internet experienced sever services breakdown for days:
I personally find it excessive that any application should depend on a third party package for a single function as simple as text padding, especially in an ecosystem fast-evolving as Node/NPM, but that’s just my personal opinion, and the rest is history.
Bottom line, if you decide that you need to install Node.js because you need some of its NPM packages, you’ll have also to accept the fact that from time to time you’ll see these vulnerabilities warning, since not all packages are promptly updated (bear in mind that most of these packages are maintained by volunteers who work on them in their free time). Unless the culprit package is abandoned, chances are that eventually it will be updated and the vulnerability resolved. But often you’ll be dealing with long dead packages, so unless the author of the package depending on the former finds an alternative package to use or, failing that, re-implements it from scratch, these warnings might end up showing for quite some time.